IdP Setup
Currently WorksAudit is designed to work with other SAML-based IdP (Id Provider) to provide user management and authentication.
Following are the steps to setup HUE >=19.06 as SAML IdP (Id Provider) to WorksAudit as SP (Service Provider):
-
Download and save the SAML metadata file from HUE IdP using the following URL:
https://[tenant]-[landscape].hue.worksap.com/idp/metadata, but replace[tenant]and[landscape]with the values of the tenant and landscape of the HUE that will provide IdP service. For example, use https://scmsystemb-develop.hue.worksap.com/idp/metadata forscmsystembtenant anddeveloplandscape. Assume that the name of the downloaded file issaml.xml. -
Go to WorksAudit Cognito User Pool for the environment (
wap-audit-cognito-user-pool-[environment]) -
Select Federation/Identity providers from the sidebar menu, then click the SAML button on the screen, an input form will be displayed.
-
Upload the
saml.xmldownloaded earlier to the Metadata document field. -
Set the field Provider name value to be
[tenant]-[landscape], e.g.scmsystemb-develop. -
Check the Enable IdP sign out flow check box.
-
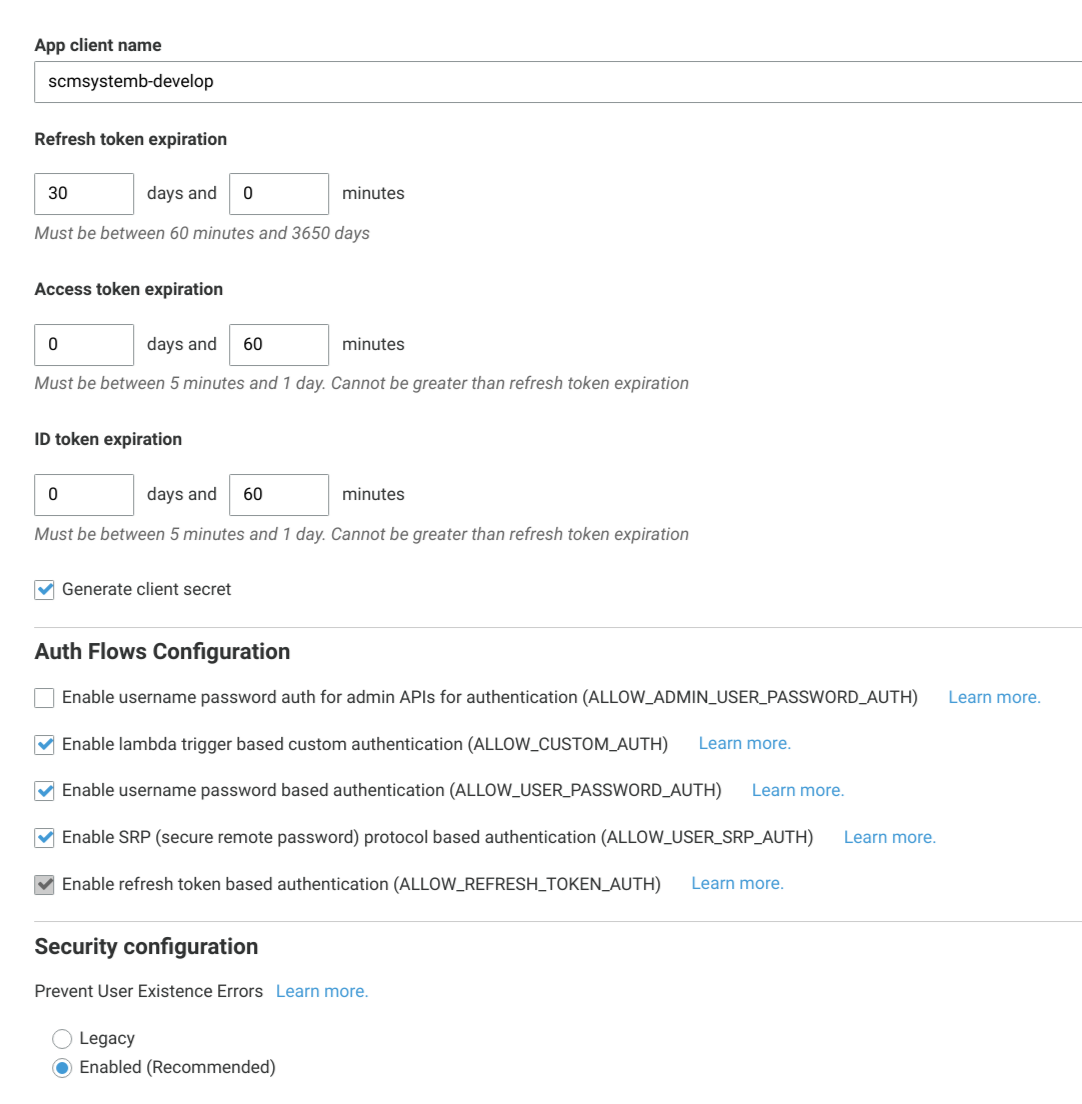
Add new App client by selecting General settings/App clients from the sidebar menu, scroll to the bottom and click on the Add another app client button/link.
-
Fill in the App client name to be
[tenant]-[landscape], e.g.scmsystemb-develop. -
Check Enable username password based authentication (ALLOW_USER_PASSWORD_AUTH)
-
Keep all others options to the default.
-
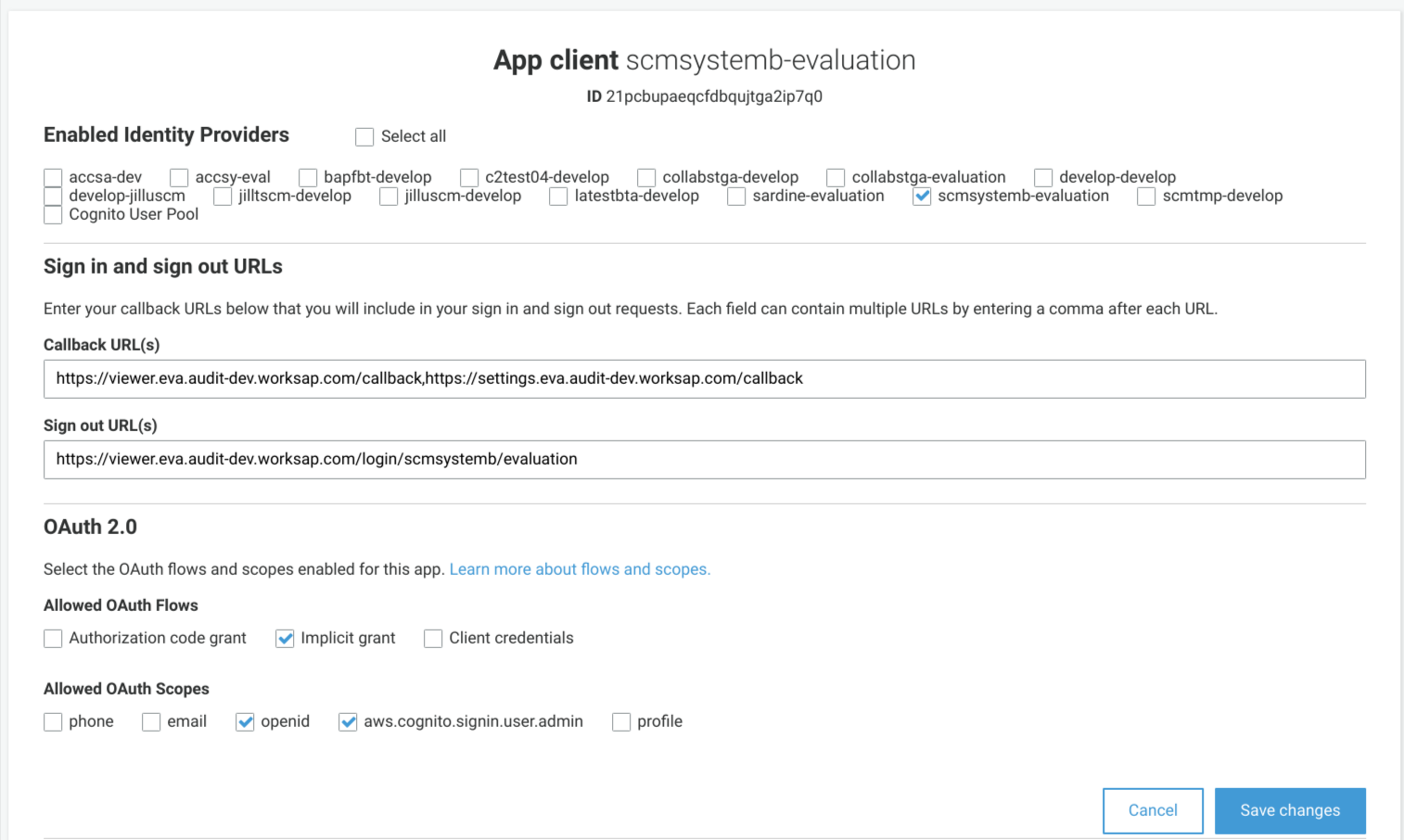
Configure the App client integration by selecting App integration/App client settings from the sidebar menu, then scroll down to the setting section for the App client that has just been created (titled App client
[tenant]-[landscape]) -
Check the Enabled Identity Providers that has exactly the same name as the App client, that is
[tenant]-[landscape]. -
Enter following value to the Callback URL(s) field:
https://viewer.[worksaudit-environment].[worksaudit-domain].worksap.com/callback,https://settings.[worksaudit-environment].[worksaudit-domain].worksap.com/callback, replace[worksaudit-environment]with a WorksAudit environment name,[worksaudit-domain]with a WorksAudit subdomain. For example:https://viewer.eva.audit-dev.worksap.com/callback,https://settings.eva.audit-dev.worksap.com/callback. -
Enter following value to the Sign out URL(s) field:
https://viewer.[worksaudit-environment].[worksaudit-domain].worksap.com/login/[tenant]/[landscape]*, for examplehttps://viewer.eva.audit-dev.worksap.com/login/scmsystemb/evaluation*. -
Check Implicit grant on Allowed OAuth Flows.
-
Check openid and aws.cognito.signin.user.admin on Allowed OAuth Scopes.
This steps are based on HUE Wiki article.
-
Open the URL for registering SP in HUE:
https://[tenant]-[landscape].hue.worksap.com/idp/swagger-ui.html, e.g. https://scmsystemb-develop.hue.worksap.com/idp/swagger-ui.html, and choosePOST /serviceprovidermetadata -
Enter a JSON for registering SP. Following JSON is an example of an SP registration:
{ "acsUrl": "https://wap-audit-eva.auth.ap-northeast-1.amazoncognito.com/*", "enabled": true, "entityId": "urn:amazon:cognito:sp:ap-northeast-1_Xry2Nso5U", "logoutRequestUrlForRedirectBinding": "https://viewer.eva.audit-dev.worksap.com/login/scmsystemb/evaluation", "logoutResponseUrlForRedirectBinding": "https://viewer.eva.audit-dev.worksap.com/login/scmsystemb/evaluation", "name": "wap-audit-env-eva-scmsystemb-evaluation" }
Notes
- This procedure should be automated.
Following steps assume that the WorksAuth keycloak realm that will be used is worksaudit-develop, WorksAudit environment target is eva and the tenant/landscape to be registered is collabstga-evaluation.
-
Login to WorksAuth administrator console for
worksaudit-develop. Please contact #env_audit channel for ID and password. -
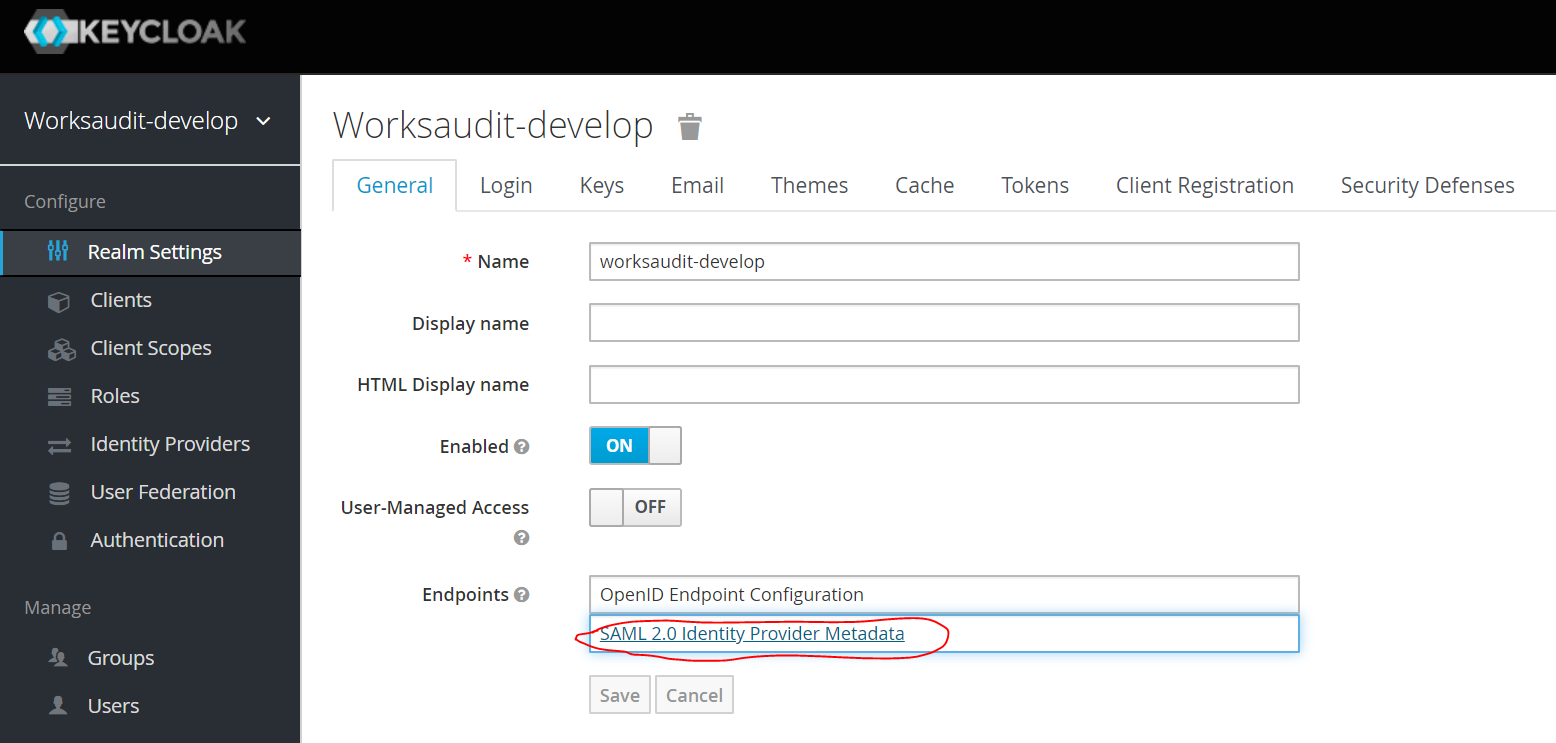
Generate SAML Identity Provider Metadata document. See following image:
-
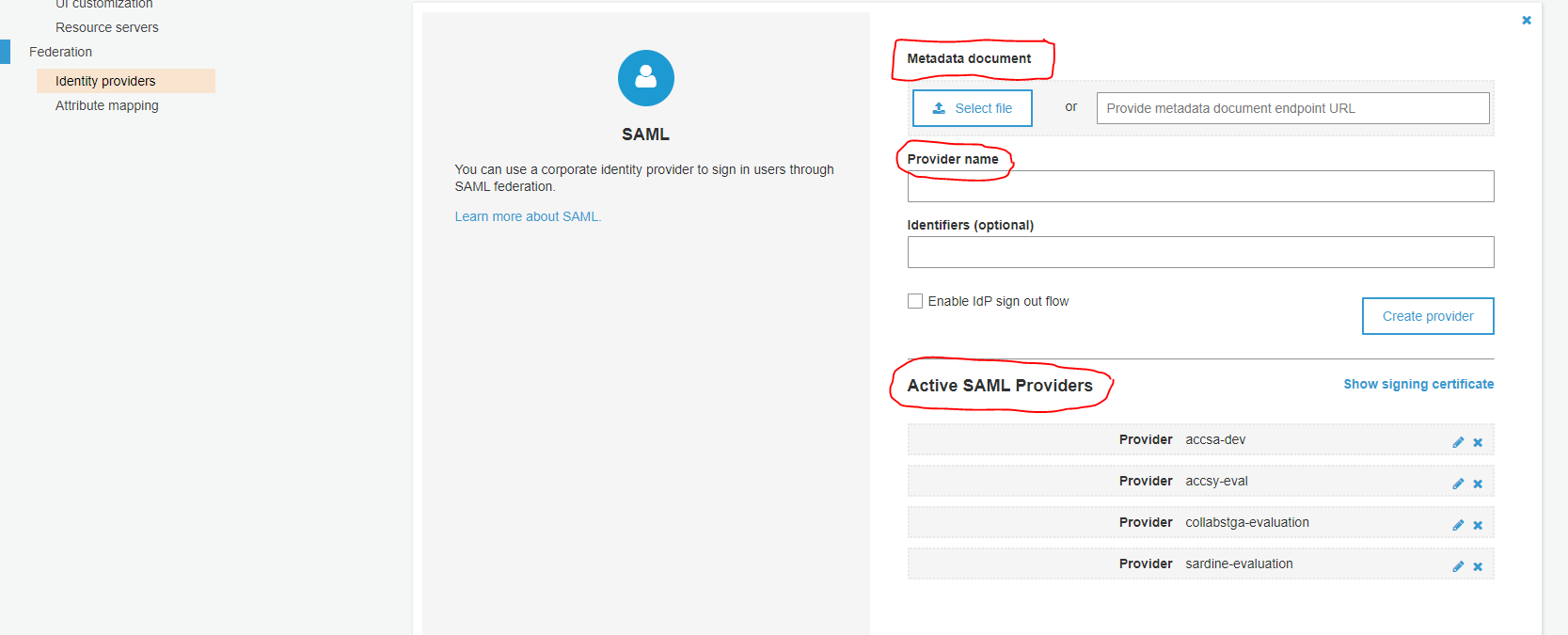
Upload SAML Identity Provider Metadata obtained in the previous step to Cognito User Pool details, as shown in the following image:
-
Set the provider name as a combination of tenant and landscape in the following format:
tenant-landscape. Check the enable IdP signout flow checkbox as shown below, then sav the provider:
-
Configure the Enabled Identity Providers, callback URL, logout URL and Allowed OAuth2.0 scopes for the app client as shown below:

-
Login back to WorksAuth administrator console for
worksaudit-develop, and create a new client as shown below.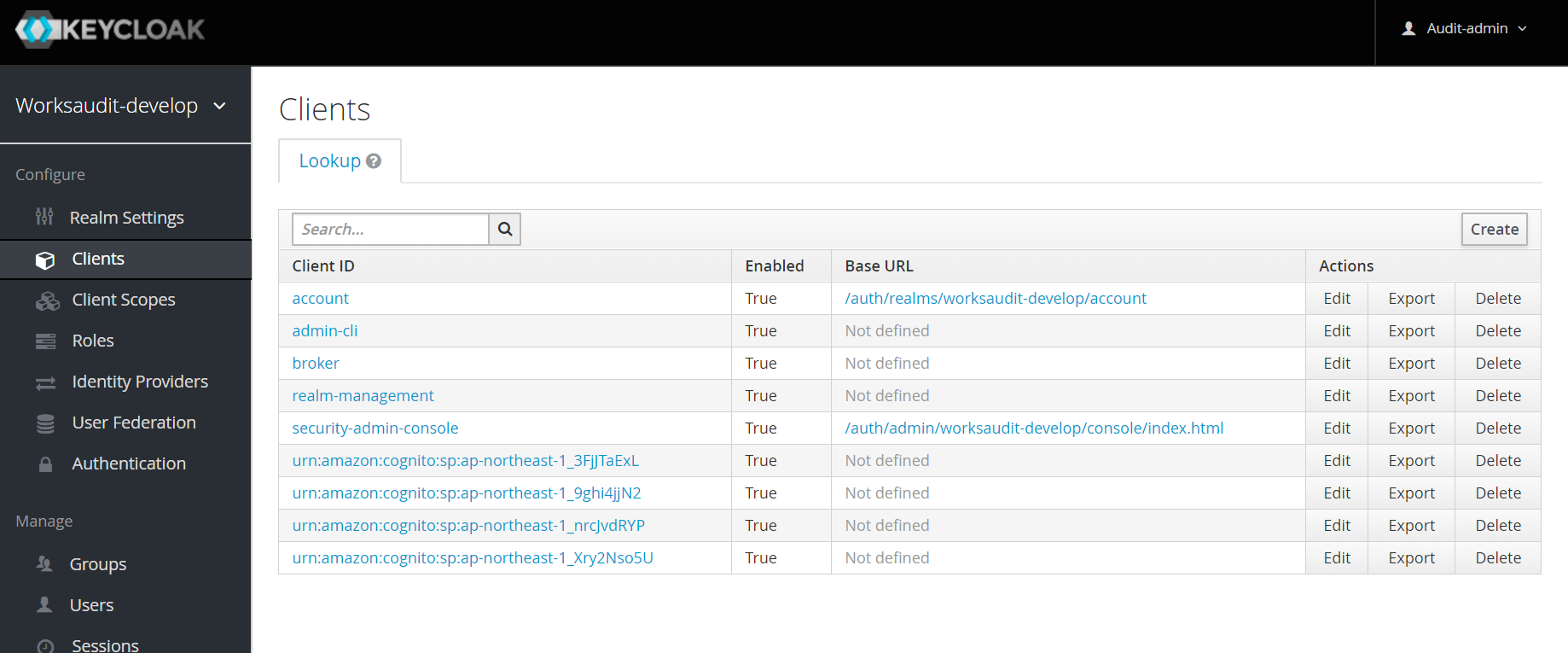
-
Enter client details
- Enter the Client ID:
urn:amazon:cognito:sp:<yourUserPoolID>where<yourUserPoolID>is the Pool Id when you click General Settings in your Cognito User Pool Detail. (see here for more information). - Change the Client Protocol to
saml.
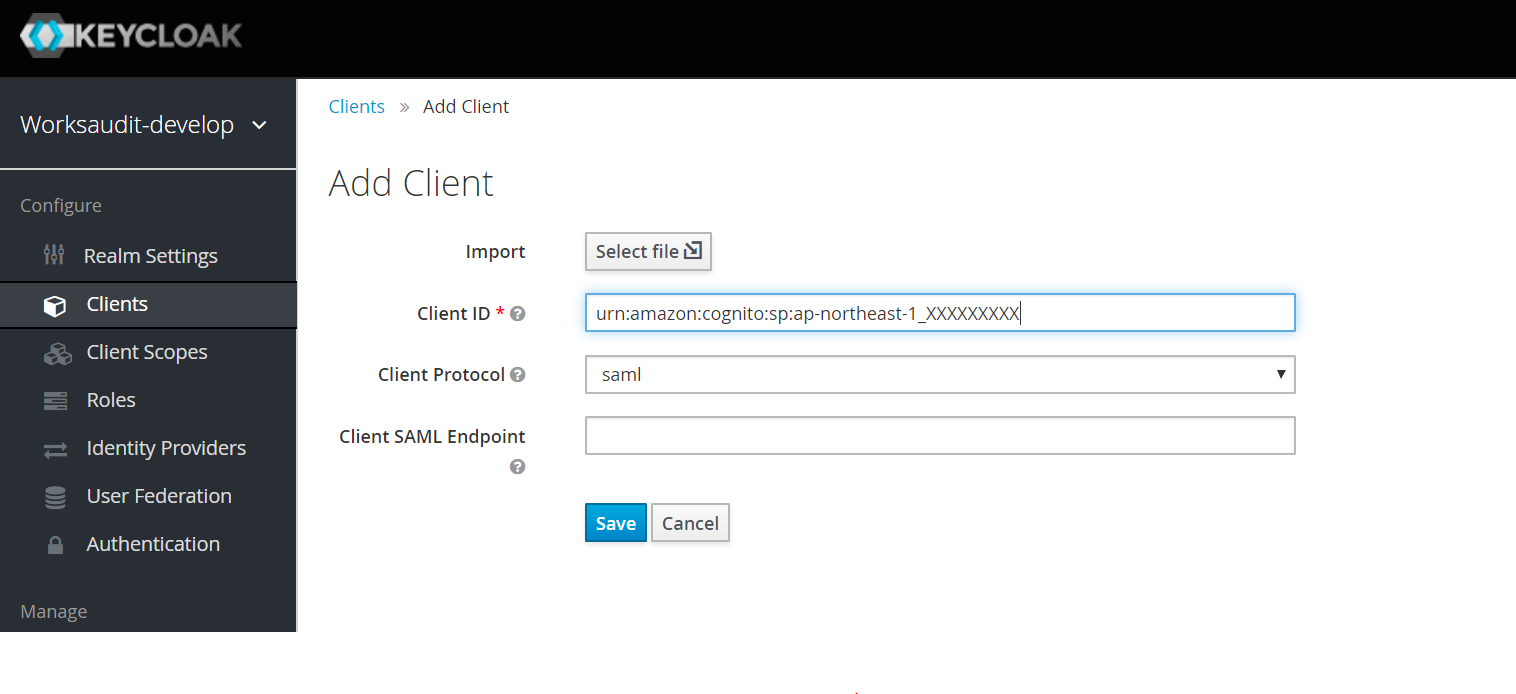
- Enter the Client ID:
-
Make following configurations:
- Change
Client Signature Requiredtofalse. - Set
Valid Redirect URIstohttps://{domain}.auth.{region}.amazoncognito.com/* - Set
Master SAML Processing URLtohttps://{domain}.auth.{region}.amazoncognito.com/saml2/idpresponse. - Set
Fine Grain SAML Endpoint Configuration > Logout Service Redirect Binding URLtohttps://viewer.{env}.audit-dev.worksap.com/login/{tenant}/{landscape}. Notes: Sometimes the Logout URL does not work. Please tryFine Grain SAML Endpoint Configuration > Logout Service POST Binding URLtohttps://viewer.{env}.audit-dev.worksap.com/login/{tenant}/{landscape}.
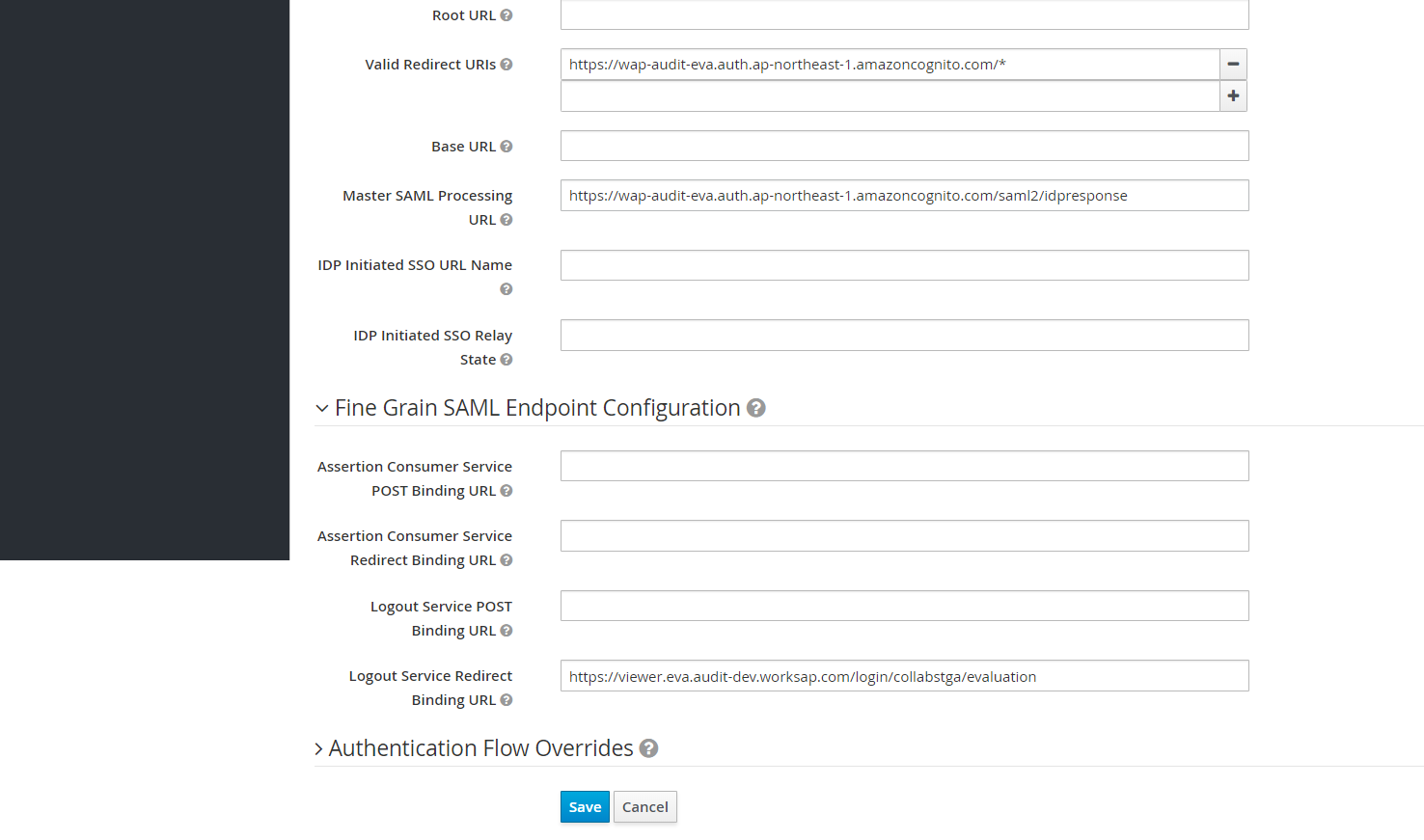
- Change
-
Add users. Click on the users tab in Keycloak and click “View all users” to see all users or “Add users” to add a new user.
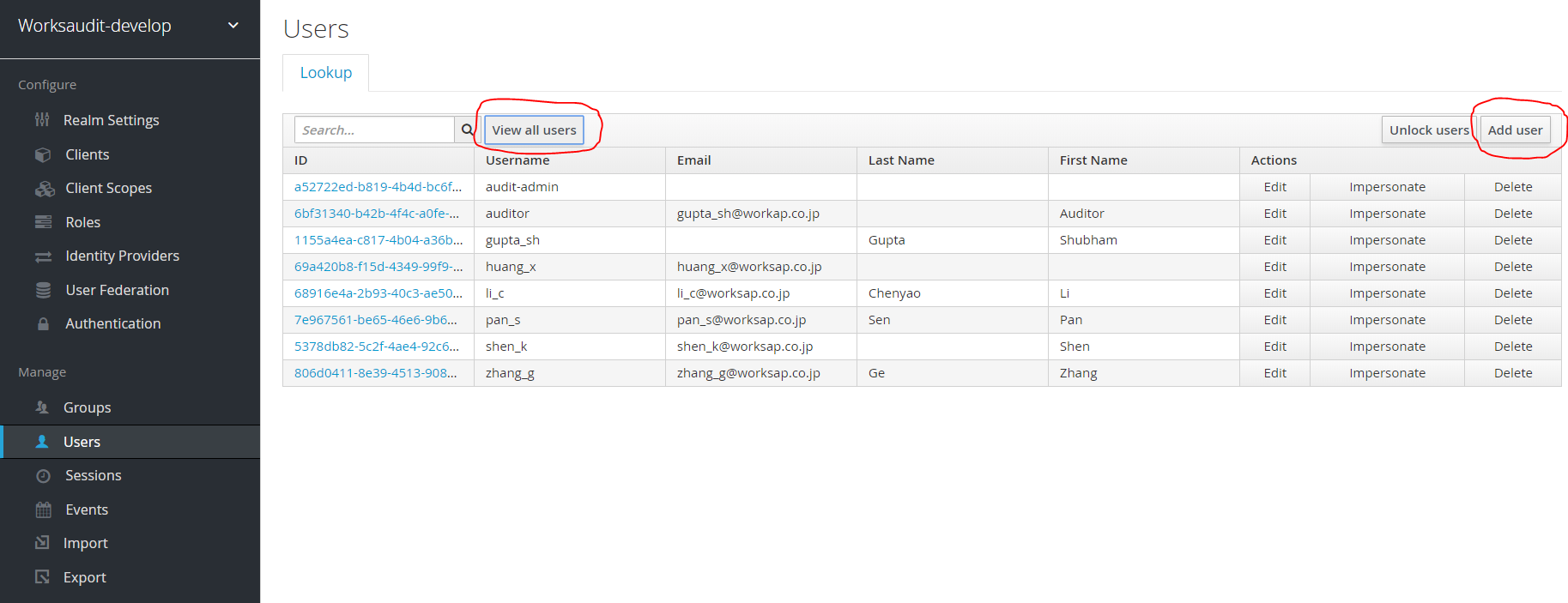
-
Manually authorize added user to WorksAudit by adding the user to a DynamoDB table called
wap-audit-user-athority-{env}. Add following entry to the table for each user you would like to authorize:{ "id": "wap/hue/user/{tenant}/{landscape}/{username}" }
- Be sure to Logout from Keyclock portal before testing the auth flow you just built. The admin account is a valid account for your system and if you did not authorize it in DynamoDB (and you should not do that) you will be logged in automatically when accessing Audit pages, skipping login credential input page, but deny to see pages with restricted access.
NOTE: This is a work in progress.
Use the IdP setup script, which provides an authomated method for seting up a SAML IdP configuration
As of the moment this doc was written the script lacks of the last part, registering SP to IdP, which need to be completed manually. Check out the documentation in the script for confirming the latest updates